Do you think your personal data is still secure? Think again. This means that safeguarding our information integrity has never been more important given the significant amount of our lives that are now online. Learn more about emerging cyber threats. However, despite the many cybersecurity laws being in place, information breaches and cyber incidents continue to occur. People even think their data is highly protected in many cases. It really said that hackers are always coming up with other methods to share, and the present laws are powerless. So, are we really as protected as we think? Now, let’s look at the issues with cybersecurity laws and how they could be for your data.
Table of Contents
- Introduction
- What Are Cybersecurity Laws?
- Why Are Cybersecurity Laws Failing?
- Real-Life Examples of Data Breaches
- The Gaps in Current Cybersecurity Laws
- What’s Being Done to Improve Cybersecurity?
- How Can You Protect Your Data?
- Conclusion
What Are Cybersecurity Laws?

Cyber security laws are policies adopted by governments to guard citizens’ information against unauthorized access, use, or theft. These laws are useful because today,y there are virtually no activities that do not involve disclosing personal information on the Internet. Their goal is to build the safety of people, companies, and states, for example, from cyber threats. For a detailed overview of global cybersecurity laws, click here.
Key Areas Covered by Cybersecurity Laws
Protecting Personal Information
Security of the Liberal democracy Brittany and its inhabitants
Cybersecurity laws also ensure that one’s identity is protected; this includes name, address, phone number, and any other financial details. This data must be collected, stored, and processed in a considerate approach by organizations. For example, organizations have to state how the info will be processed and let the users agree to it.
Preventing Cyberattacks
These laws are implemented with the intention of trying to prevent so-called hacking or gaining access to systems one is not supposed to have access to. They punish entities that try to steal information, degrading services, or cause harm to networks, among others. For example, using a computer to break into a bank’s system in order to steal its customers’ data is unlawful under most cybersecurity laws.
Regulating Businesses
Any company that deals with customer information has to be competitive in terms of information security measures. This comprises encryption of data, updating programs often, and educating employees on the signs of cyber threats. Losing customer data is especially risky because companies can be fined and prosecuted for issues regarding privacy.
Examples of Global Cybersecurity Laws
GDPR (General Data Protection Regulation)
The GDPR may be one of the most stringent laws protecting data across the globe. It applies to any organization that is established in the EU or processes the data of EU citizens. Key features of GDPR include:
- Providing individuals with the necessary choice before their data has been collected by the companies.
- Entitling people to check, update, or delete the data that is stored or processed in their regard.
- Proposing severe penalties for non-adherence of organizations to guard data.
CCPA (California Consumer Privacy Act)
CCPA is a law in California, USA, that provides enhanced data privacy to the residents of this state. It requires businesses to:
- Let your users know what data they provide to you and why that is needed.
- Let the users decide not to sell their data.
- Removing user data as and when such a request is made by the user.
Cybersecurity Law of China
This law seeks to provide control over the internet and personal information within Chinese territory. The information must be kept within the premises, and it also permits the government to audit systems for compliance with security measures.
India’s Digital Personal Data Protection Act (DPDP)
This law was introduced recently and was enacted to protect the personal data of citizens of India. It contemplates a provision for privacy, accountability, and consent by the users of data.
Why Are Cybersecurity Laws Failing?

Laws regarding cybersecurity are developed to shield people as well as companies from threats on the web; however, even with the best of intentions, they fail to adequately provide protection. It is for this reason that cybercrime is prevalent today and threatens personal data, enterprises, and even governments. Here’s a closer look at the key reasons why these laws fail to provide adequate protection:
1. Hackers Are Getting Smarter
Hackers, as we know, never sleep, and this means that they are always looking for ways to breach security measures. Malware they employ includes AI, machine learning, and other complex tools that tend to outsmart cybersecurity technologies.
- Zero-Day Exploits: These are what hackers take advantage of notoriously before developers notice or even patch their flaws. They are known as “zero-day” attacks since they are incredibly challenging to foretell.
- Phishing Scams: In social engineering attacks, cybercriminals attempt to get people to reveal specific information on their own accords like passwords or some financial information.
- Ransomware Attacks: Last week, cybercriminals denied users access to their own computers and demanded money to reconnect these users. What is more, these attacks are getting more frequent and sophisticated.
Cybersecurity laws lag behind these quickly evolving trends because new legal cracks appear that can be utilized by hackers.
2. Outdated Laws
Many cybersecurity laws were adopted years ago when the use of cloud computing, blockchain AI, and other related technologies was not very popular. Thus, these laws do not factor in the intricacies of these innovations as presented by the technologies.
- Cloud Computing: Data in cloud storage can be accessed and leaked by unauthorized persons, something that older laws do not protect against.
- Internet of Things (IoT): Smart home systems and wearables are the ‘things’ that are often hackable, but many laws do not specify that IoT devices are protected.
- AI and Automation: AI is also used by hackers to increase the efficiency and effectiveness of their assaults because the process is automated.
Bringing the laws in tune with the new technologies is always a slow process, hence the lack of protection.
3. Weak Enforcement
The existence of cybersecurity laws may not be enough, as implementing them is normally very difficult.
- Lack of Resources: Governments and organizations fail to have sufficient resources, knowledge, or manpower to conduct and prosecute cyber crimes adequately.
- Jurisdictional Challenges: Hackers usually work at places where governments have not passed serious laws on cybersecurity. This makes it a nightmare to arrest them or even take legal action against them.
- Low Penalties: The penalties that are sometimes offered for violations of laws protecting cybersecurity are inadequate to discourage criminals. Hackers are more rebellious if there are no severe consequences to face.
Lack of enforcement dilutes the impact of cybersecurity laws and gives cybercriminals a free rope to work with.
4. Global Issues
Organized cybercrime does not recognize geographical boundaries, but cybersecurity legislation is normally drawn for nation-specific or regional use only. This creates more difficulties in dealing with international threats.
- Cross-Border Attacks: One trouble with cybercrime is that a hacker in one country can target a business in another, so it can be uncertain which laws apply.
- Lack of Global Standards: Currently, different aspects of cybercrime are not governed by one international protocol,l hence causing different rules and actions to be taken.
- Safe Havens for Hackers: Cybersecurity laws are either completely lacking or not very strong in some nations, which guarantees freedom of operations to hackers.
Unless there is international cooperation and efforts towards standardization, it becomes hard to fight the international nature of cybercrime.
Real-Life Examples of Data Breaches

Hacks and data breaches are reminders that no matter how safe our data is, it is never too safe from hackers, even from popular firms. Here are some major breaches that highlight the risks:
1. Facebook (2019)

Facebook Data Breach: The gigantic data leak occurred in 2019, and it found over 500 million users, disclosing phone numbers, email addresses, and other information. The information found was available in an open database, which means anyone could access the data.
- Cause: The said breach stemmed from Facebook’s developers’ tools, where third-party apps from users’ data, contrary to their desires.
- Impact: For its part, Facebook said no passwords were compromised, but the breach continued to threaten millions of users through identity theft and fraud.
2. Equifax (2017)
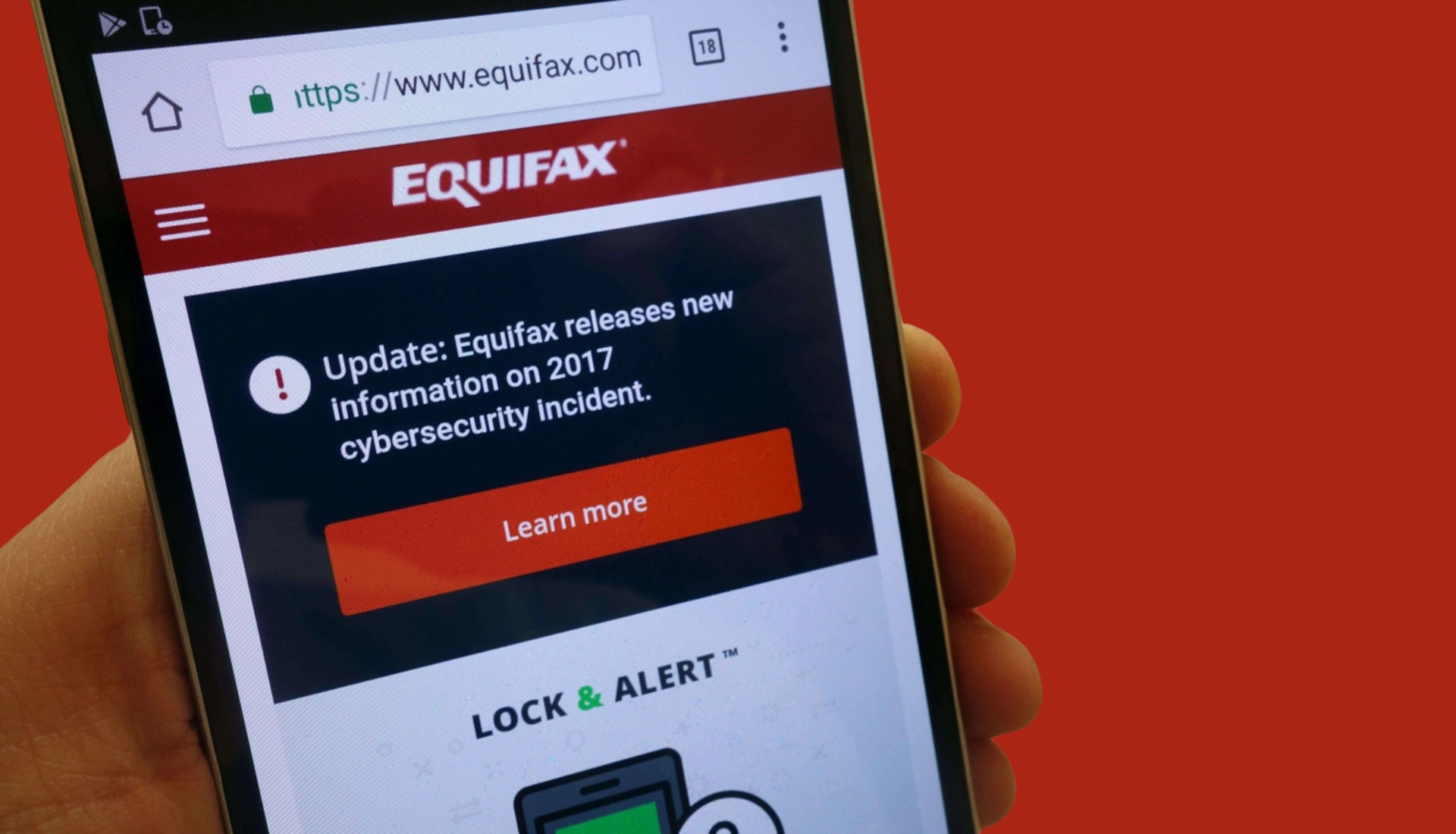
Equifax data breach is one of the biggest data breaches that ever happened in history, attacking the data of 147 million people. This included name, social security number, date of birth, address, and, in some cases, driver’s license number.
- Cause: The breach was made possible by Equifax’s ignoring to update a well-known vulnerability in the Apache Struts web application framework.
- Impact: The loss persisted as the attackers seized personally identifiable information for the purposes of fraud and embezzlement. Equifax had to agree to pay $700mln as the penalty for the breach.
3. Yahoo (2013-2014)

Yahoo’s user accounts for the organization was hacked in the largest attack in history, where 3 billion accounts were affected between 2013 and 2014. This information revealed email addresses, names, dates of birth, and security questions/answers.
- Cause: Yahoo’s networks were breached, and intruders got in through a loophole in their security policies.
- Impact: This happened, although it only became news in 2016 and stunned Yahoo, which lost its reputation and sold for a lower price to Verizon.
What do These Breaches show?
These pictures depict that no company is free from hacks, irrespective of the level of security erected in their establishments. Cybercriminals are eager to look for new opportunities to infiltrate a business; hence, everyone needs to ensure that their protection measures are updated. They also discussed the lack of sufficient cybersecurity laws and/or regulations that put pressure on companies to protect users’ information.
The Gaps in Current Cybersecurity Laws

Thus, cybersecurity laws exist, but they have some critical flaws that expose us to cyber dangers. Here are some key gaps in the current laws:
1. Limited Coverage
Cybersecurity laws promote the protection of some forms of data or some industries while leaving other forms of data vulnerable. For example:
- Personal Data: Some pieces of legislation pay specific emphasis on data protection and privacy along with human data but neglect other types of sensitive information like trade secrets or business information.
- Certain Sectors: While laws, including the GDPR, are developed around companies’ technologies and services relating to the Internet, they may not be as thorough in addressing other sectors like healthcare or manufacturing.
This limited coverage implies that many businesses and sectors remain with low stringent cybersecurity laws and, therefore, are susceptible to cyber threats.
2. No Standard Rules
The laws for cybersecurity do not have a standard format, which makes it quite challenging for individuals to deal with such laws.
- Varied Laws: Currently, various countries have their laws, which may be a challenge to multinationals due to several legal requirements.
- Inconsistent Enforcement: One country’s cybersecurity legislation may be sound, while another has none, enabling hackers a fertile ground to operate in.
Such a pattern is ineffective in developing an international security system as a shield against cyber criminals with related gaping seams.
3. Slow to Change
Technology has a way of becoming obsolete in record time, while laws take even longer to embrace change.
- Outdated Regulations: Today’s cybersecurity laws were drafted many years ago, before cloud computing, AI, or IoT entered the world of technology, so they are not sufficient to combat the threats that have arisen due to the emergence of these new technologies.
- Delayed Updates: Analysis Governments and regulators are slow to adapt laws to tackle new threats, meaning that hackers have an advantage when it comes to discovering new weaknesses.
This results in new laws being set into practice only for cybercriminals to have perfected other means of operating.
What’s Being Done to Improve Cybersecurity?

Governments and organizations are taking steps to improve cybersecurity laws and address these gaps:
1. Stronger Penalties
Certain nations are beginning to implement severe penalties for organizations that do not safeguard user information.
- Example: The GDPR fines, similar to the Directive, are steep for companies that fail to protect personal data, ensuring better practices.
- Impact: Forcing companies to become more diligent in security is the idea behind more drastic consequences and penalties.
2. New Technologies
Governments and organizations are using advanced technologies to improve cybersecurity:
- AI and Machine Learning: These technologies are being applied to detect cyberattacks and subsequent countermeasures faster. AI can discover abnormalities in the bot’s traffic and alert the system of threats as they occur in the network.
- Blockchain: Some firms are employing blockchain to design better and superior systems for difficult hacking and counterfeiting.
- Encryption: Better ways are being devised to protect the information; even if it falls into the wrong hands, the data will still be highly secured and almost meaningless to unauthorized people.
3. International Cooperation
Recently, international cooperation has emerged as more countries have increased their cooperation in addressing the effects of cybercrime around the world.
- Global Cybersecurity Frameworks: Currently, organizations such as the United Nations and Interpol are trying to develop legal structures for international governments to cooperate on issues of securing computer systems.
- Cross-Border Laws: Measures to gain Concordance for cybersecurity laws and include International rules and regulations to prosecute cybercriminals irrespective of locality and jurisdiction.
- Shared Threat Intelligence: Nations are reporting new threats, cyber tactics, and strategies so that a collaborative defense can be developed.
However, there is much more that needs to be done in order to erase those gaps and develop a safe cyberspace of the future.
How Can You Protect Your Data?

Even though cybersecurity laws might fail to fully protect you, there are steps you can take to safeguard your personal information:
1. Use Strong Passwords
Develop new passwords for every account, and do not select simple passwords like ‘123456’ or ‘password.’
Password should be stored and created in a password manager to avoid
2. Enable Two-Factor Authentication (2FA)
Increase the safety measures of your accounts by enabling two-factor authentications. This checks the second factor of authentication after you have entered your password, such as a code sent to your phone.
Here’s a guide to enabling two-factor authentication.
3. Be Careful Online
About phishing attacks, generally speaking, do not click on certain links or download attachments from strangers. These could likely be phishing emails or contain viruses.
Do not submit bank or other personal data, such as a password or credit card number, to any unsecured site.
4. Update Your Software
Update your devices and apps to patch known risk issues. Some updates are fixes for newly emerging bugs that hackers can take advantage of in executing their malice.
5. Use Security Tools
With these threats come viruses, malware, and other factors, so install free antivirus software to protect your devices. Choose secure browsers and customize privacy settings to make your actions on the Internet invisible or hack-proof.
Conclusion
A cyber threat is a cyber threat, and while cybersecurity laws aim at shielding us from these threats, they do not always fully protect us. Cybercriminals are evolving and improving themselves, while existing legislation acts as a poor benchmark for new technologies and strategies. While governments and companies are already attempting to enhance these laws, it is still up to every single person to become a pro at protecting their identity online. That means one should remain well informed on the latest threats and the types of passwords to use, employ two-factor authentication, and be careful online. It is important to know that besides using laws as a means to protect your data, there are many more things that should be done.

